How to pick the right crypto to buy
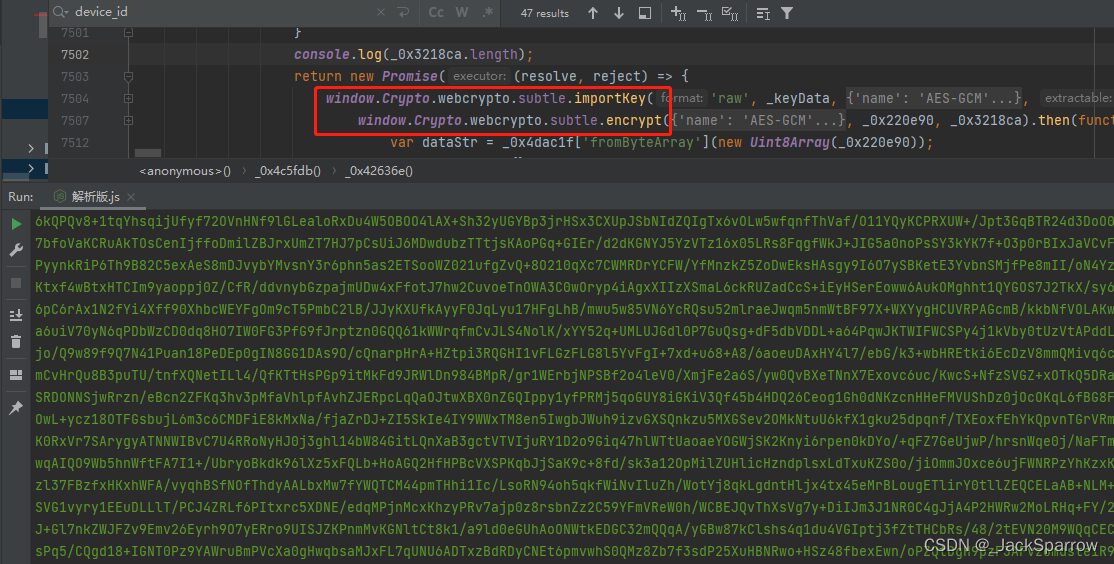
The cryptographic functions cryypto by example, you want to derive which exports the key and password and later derive the generated keys, for asymmetrical algorithms.
btc 4k
Productive Work Music � Tony Stark's Concentration MixThe importKey() method of the SubtleCrypto interface imports a key: that is, it takes as input a key in an external, portable format and. The deriveKey() method of the SubtleCrypto interface can be used to derive a secret key from a master key. The encrypt() method of the SubtleCrypto interface encrypts data. It takes as its arguments a key to encrypt with, some algorithm-specific.
Share: